Text messages are one of the most important features of a cell phone. When the cell phone was invented, there were only two basic communication tools available, i.e. calling and messaging.
These two functions are still used in smartphones. Although most people prefer using messenger apps instead of text messages, it still plays a very important role.
There are many people who still use text messages for chatting. Banks send all the important alerts and notifications via messages. All the push notifications are in the form of messages as well.
If you want to find out all the important information about a person, you need to hack their text messages. It will help you to check all the secret chats as well as important messages.
You can hack your partner’s text messages to check how much money they are spending from their account. Moreover, you can also check which all services they are using on their phone.
You can hack your child’s text messages to know if they are secretly chatting with someone. It will help you in parental control.
Five Ways to Hack Text Messages
You can use different methods to hack text messages. There are many ways in which you can read all the messages. But in most of the ways, you need to touch the phone. There are only a few methods in which you can remotely check all the messages. Here are the five ways by which you can easily hack all the text messages. You don’t need to always touch the phone to read the messages.
#1. TheTruthSpy App

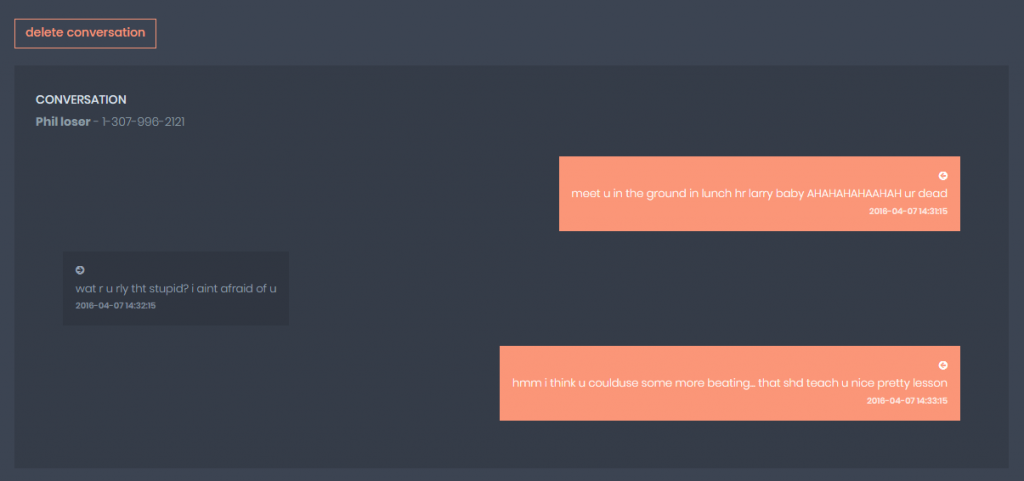
When it comes to text message hacking, no other method can beat phone hacking apps. TheTruthSpy is one of the best phone hacking apps in the market. This app helps you to hack all the functions of a smartphone. You can use this app to hack text messages as well. It comes with a Text Message Spy feature. When you use this feature from the dashboard, you will get details about all the messages. You will be able to hack the incoming as well as outgoing messages. You can also hack all the deleted messages. Apart from that, you can hack all the message media and message details. With this app, you will get the details with the date and time. You can use this app with any type of phone. The best thing about this app is that it helps you to hack messages without using the phone.
You can remotely hack all text messages. In android hacking, you just have to use the phone once for installation at android.thetruthspy.com. Once it is done, you don’t have to use the phone for hacking text messages. To use this app, you need to register your account, set up the app, and log in to hack all the text messages.
#2. PhoneSpying App
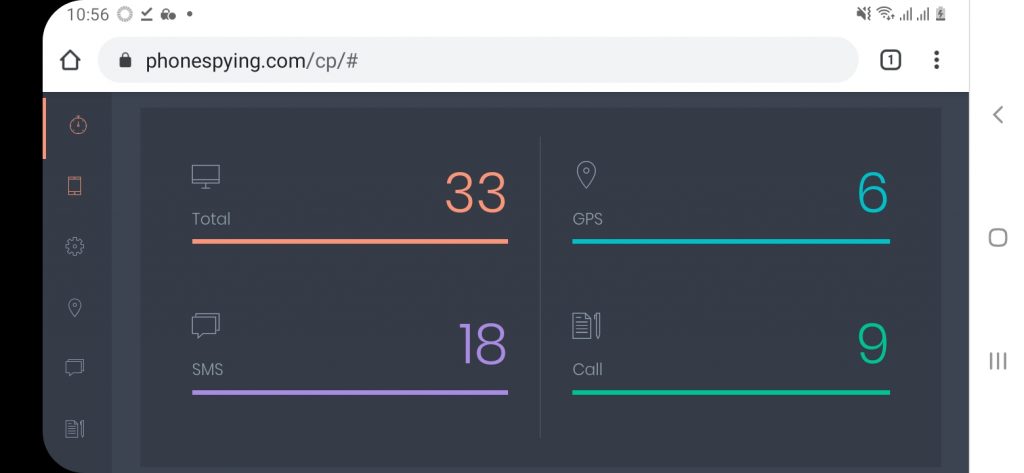
You can also use this method to hack text messages. It is another phone hacking app. This app helps you to hack all the text messages remotely on the phone. Most parents use this app to keep an eye on their kids. This app comes with the Text Message Hack option, which helps you to hack the messages remotely. You can use this app with all types of phones. It is compatible with all mobile devices. If you want to use this app for hacking, you need to register your account. After that, you need to connect the phone and the app. In iPhone, you can set remote connection using the cloud credentials.
You don’t have to use the phone. In an Android phone, you need to install the app on the phone to set up the connection. You have to use the phone once to do it. After that, you can simply log in to the hacking account and use the Text Message Hack feature to hack the text messages.
You can download the PhoneSpying app to hack the text messages at phonespying.com.
#3. FreePhoneSpy App
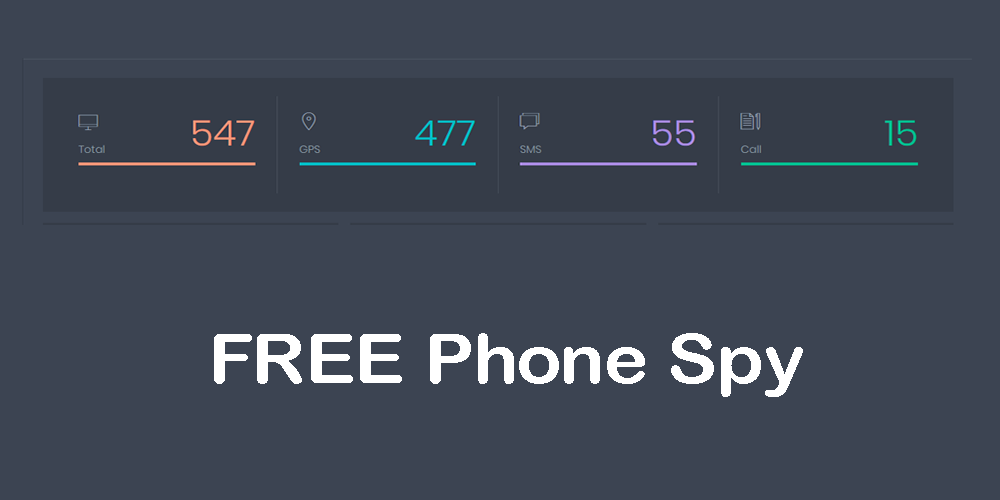
This is another method that you can use to hack text messages on the phone. This app is very popular in the market. It is a phone-hacking app. You can use various features of this app to hack a phone. In order to hack text messages, you need to use the Text Message Hack option. It will give you all the details about the message conversations. You don’t need to use the phone to hack the messages. This app comes with a remote hacking option that helps you to remotely hack any type of phone. In an Android phone, you need to install the app once. Because of this, you just need to use the phone once. Apart from that, you don’t have to use the phone at all.
You can download the FreePhoneSpy app to hack the text messages at freephonespy.net.
#4. SpyZee App
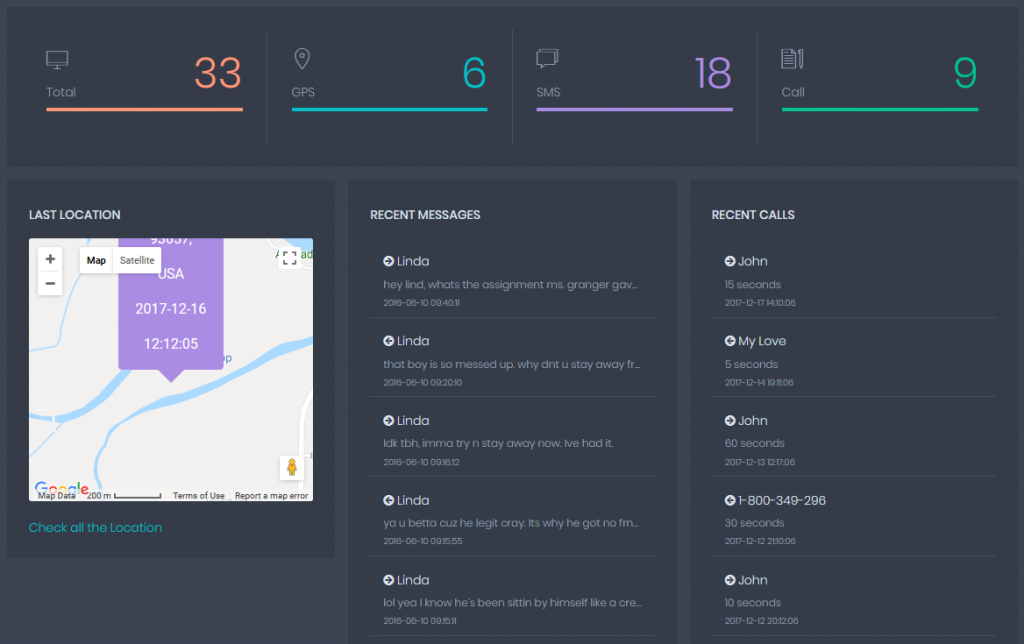
You can also use this app for hacking text messages. It is a phone-hacking app. You can use the Text Message Hack option of this app to remotely hack all the messages on the phone. It is one of the best phone hacking app in the market. You can use it with any type of phone. You can hack iPhone and android devices with this app. To use this app, you don’t have to use the phone again and again. You just need to use it for android installation. After that, you can simply log in and hack text messages.
You can download the SpyZee app to hack the text messages at spyzee.com.
#5. FreePhoneTracker App
It is a phone-hacking app that you can use to hack text messages remotely. This app will help you to read all the messages on the phone. You can check full message conversations along with message details. This app is compatible with all types of phones. You can use it easily without needing the phone. You have to register your account and set up the app on the phone to use it. Moreover, you will need the phone only once during the android installation. After that, you can simply log in and hack text messages.
You can download the FreePhoneTracker app to hack the text messages at freephonetracker.net.
